Consider the following typical block code of encryption initiation using Cipher on Java:
Key key = KeyGenerator.getInstance("AES").generateKey();
Cipher encipher = Cipher.getInstance("AES");
encipher.init(Cipher.ENCRYPT_MODE, key);

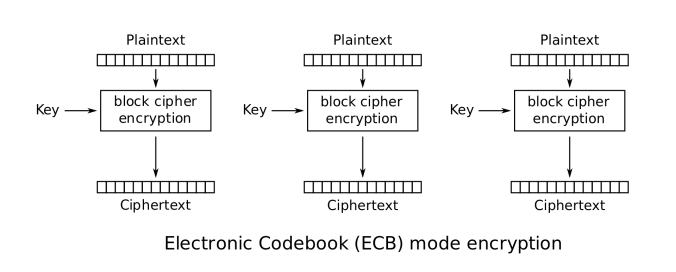
Where is the problem? The main issue is that according to the Oracle manual if you don’t specify encryption mode explicitly, it will use ECB encryption mode by default.
The full encryption schemes in these cases:
- AES: AES/ECB/PKCS5Padding
- DES: DES/ECB/PKCS5Padding
- 3DES: DES/ECB/PKCS5Padding
Actually, ECB encrypts identical plaintext blocks into identical ciphertext blocks, it does not hide data patterns well. In some senses, it doesn’t provide serious message confidentiality, and it is not recommended for use in cryptographic protocols at all.
A striking example of the degree to which ECB can leave plaintext data patterns in the ciphertext can be seen when ECB mode is used to encrypt a bitmap image which uses large areas of uniform color. While the color of each individual pixel is encrypted, the overall image may still be discerned, as the pattern of identically colored pixels in the original remains in the encrypted version.
I wrote a simple example of demonstration of such kind of attacks.
@Test
void ecbEncryptionTest() {
//Encryption provider initialize
EncryptionKeyProvider keyProvider = new TripleDesEncryptionKeyProvider();
EncryptionService encryptionService = new TripleDesEncryptionService(keyProvider);
//read the image
PlainFileEntity secretImage = FileUtil.read(RESOURCES_FOLDER + "secret1.bmp");
//encrypt the image
byte[] encryptedImage = encryptionService.encrypt(secretImage.getContent());
//set image content
secretImage.setContent(encryptedImage);
//Encrypted Image for Analysis
final String encryptedSecretPath = RESOURCES_FOLDER + "secret1_encrypted.bmp";
//save encrypted image
FileUtil.save(secretImage, encryptedSecretPath);
assertImageExists(true, encryptedSecretPath);
}
In that case the image before the encryption:

And after:

That may cause many problems, if you, for example, encrypt database content using such kind of schema. In that case even simple analysis of the encrypted text will compromise all the protected content, especially in case of encryption a lot of data using ECB mode.
As for example, let’s remind the story of “The Greatest crossword puzzle in the history the world“, which caused to disclosure of 153 million Adobe Users emails, encrypted passwords and password hints.
As for conclusion:
- Do not white your own encryption logic if possible, use approved encryption service (For example, HashiCorp Vault Transit Engine)
- Do not use ECB mode for encryption and always specify full encryption scheme, ex: AES: AES/CBC/PKCS5Padding
- Use NIST approved algorithms only
Github project reference: